Cybersecurity Best Practices
Cybersecurity tips to help you understand threats and identify opportunities for improvement.
Gmail and Apple begin enforcing stricter email requirements for delivery. Are you in compliance?
With 90% of email users worldwide now getting their email through Gmail, Apple, or Yahoo, the new deliverability standards announced by the three email giants...
Top 10 Reasons Midsize Organizations Use a Co-Managed IT Service Model
In today's technology-driven business environment, the effective management of IT resources and infrastructure is paramount to a company's success. For larger...
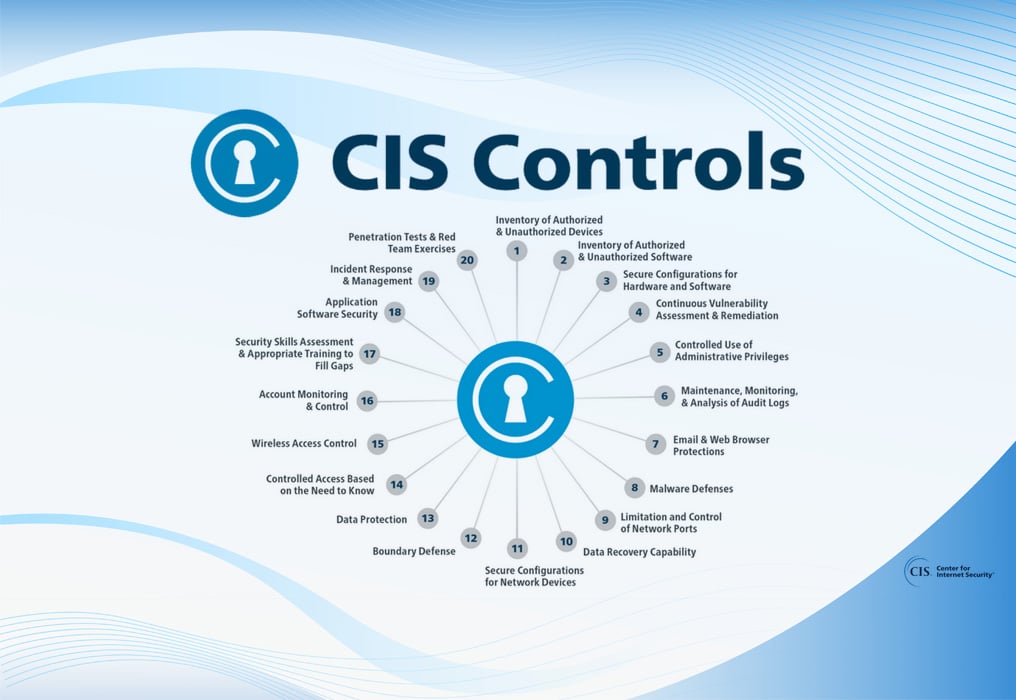
Why MSPs Should Implement the CIS Controls
There’s often a major disconnect between businesses and their Managed Service Providers (MSPs) over one key issue: cybersecurity. Many businesses believe their...
A Guide to Evaluating Your Managed Service Provider (MSP)
Today, many businesses work with a Managed Service Provider, more commonly referred to as an MSP. MSPs play an important role in augmenting the capacity of...
How to Find an MSP That’s a Right Fit For Your Organization
Today, many IT departments at Small to Midsize Businesses (SMBs) find themselves in a near-impossible position. Their team has never faced more challenges,...
Anatomy of a Breach, Client Case #2: The Importance of Security Awareness Training
In this second edition of our series, Anatomy of a Breach, we take a look at how much damage a phishing email can cause. Using a real-world example, we’ll also...
Anatomy of a Breach, Client Case #1: The Importance of an Incident Response Plan
In this first edition of our series, Anatomy of a Breach, we take a look at a client of ours who suffered from a breach but did not have a response plan in...
Why Recent Attacks Have Many Businesses Seeking Extra Microsoft 365 Security
If there’s one threat that never goes away, it’s cyberattacks. It’s a risk every organization, from the world’s largest businesses to small family-run...
Cloud Security Monitoring: What To Monitor and How Much Time You Should Spend On It
Today, practically every company and organization leverages the power of cloud computing in some way. Whether that’s through working together in real-time...
What is Endpoint Protection? A Guide to Endpoint Protection Tools for Businesses
The importance of endpoint security has grown in recent years, driven by both the widespread adoption of remote work and the growing sophistication of...